# 1. 安裝
1. 下載安裝文件
~~~
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.2.0/aio/deploy/recommended.yaml
~~~
2. 修改dashboard的service為nodeport,可以被外部訪問
```
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30002
selector:
k8s-app: kubernetes-dashboard
```
3. 部署dashboard
```
kubectl apply -f recommended.yaml
```
4. 創建serviceAccount
```
kubectl apply -f dashboard-serviceaccount.yaml
```
```
vim dashboard-serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: dashboard-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
```
創建一個serviceaccount,會自動生產一個secret,保存對應的token
```
[root@master serviceAccount]# kubectl describe secret $(kubectl get secret -n kube-system | grep dashboard-admin | awk '{print $1}') -n kube-system
Name: dashboard-admin-token-hccf9
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: cb2ed2ae-e9c2-4539-ab51-b86a29598da2
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkdFckVOWVhDQkRvWnFIZ3FuSDhFa2ZfeUkxZzJ0YzVXVGFTYzFlckcxRWsifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4taGNjZjkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiY2IyZWQyYWUtZTljMi00NTM5LWFiNTEtYjg2YTI5NTk4ZGEyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.LTiKOJu7tkPN_Vn4zFfnnKWR2SqzzOGTZn-9dcLskZYKLTQuBy_x2Pzre7aLYv4T_zFDZqxXKH-HG6-5ujFjApXv3lptVJAz2-UcsdUmgMMJ3jGt6yjIscMYPu5ZKTHVs9otDYpB8NPe5IHQUPRLAcQSmvMBtSTKqVfsP7nVDB46A_rIGFpZHnMiW2iQKnREx9ynIGyJQQW-t4pqSAwuxAQdXckQt53dKlqQ6KX7yH1b-FaaNoegt1onJdMolC54VXxS0dYKcjWa81mrcZ0wDLDIGw1hj4wAEYPNzrBh0QvN16XQmcjz2lBcz-MDdbzPg-tpcyZFo-TU1x_ohKCICQ
```
5. 獲取serviceaccount對應的token
```
kubectl describe secret $(kubectl get secret -n kube-system | grep dashboard-admin | awk '{print $1}') -n kube-system | grep ^token | awk '{print $2}'
```
輸入token登錄
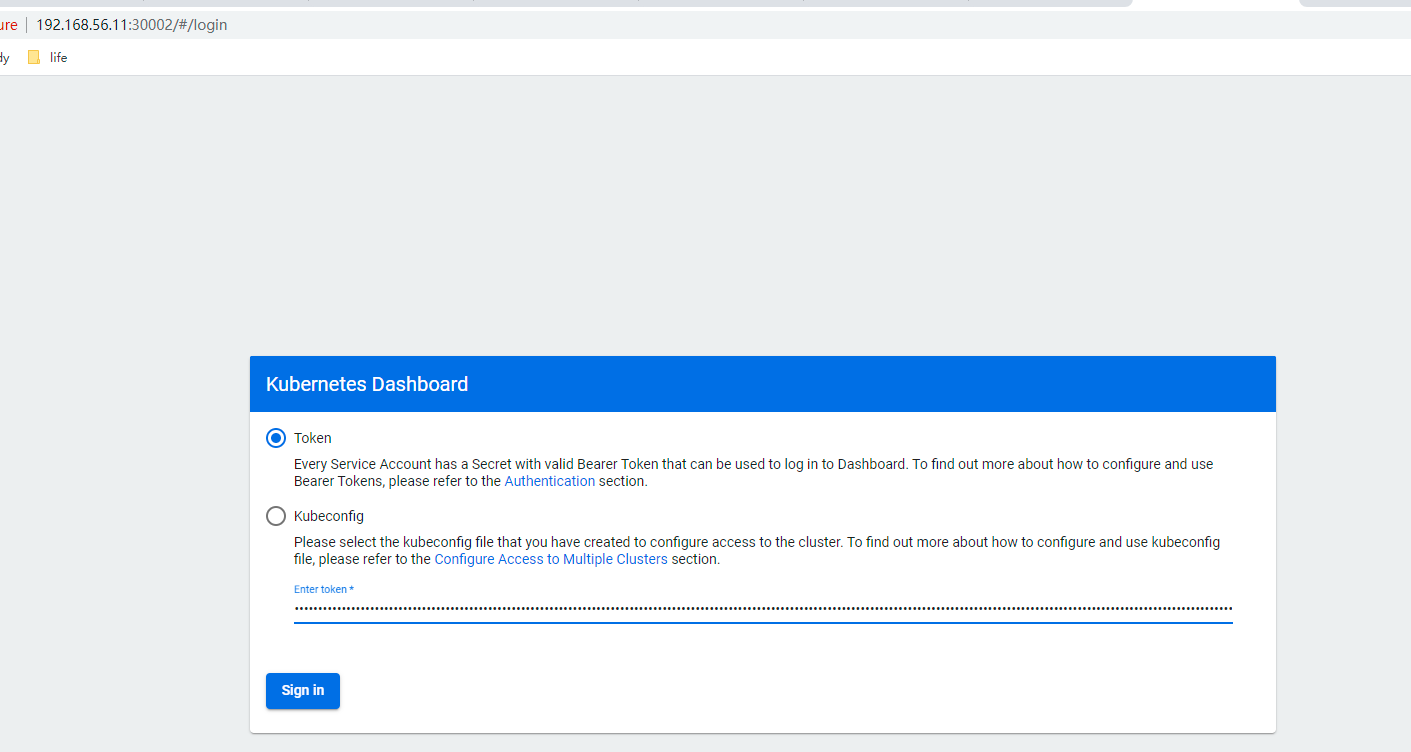
# 2. 登錄方式配置
有token和配置文件登錄方式,因為dashboard是以容器化的方式運行,所以兩種方式需要serviceAccount賬號
## 2.1 token訪問
**1. 創建serviceaccount,pod訪問賬戶**
```
kubectl create sa dashboard-admin -n kube-system
```
創建serviceaccount時,會自動創建對應的secret
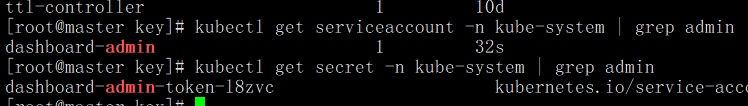
**2. 給serviceaccount綁定角色**
```
kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
```
**3. 查看dashboard-admin的secret名字**
```
ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk '{print $1}')
```
**4. 打印secret的token**
```
kubectl describe secret $ADMIN_SECRET -n kube-system | grep ^token | awk '{print $2}'
```
## 2.2 配置文件訪問
## 2.3 分級訪問
通過綁定rolebindding和clusterrolebindding,區分權限,也可以自定義role來細分權限
- docker
- docker安裝
- 數據持久化
- 鏡像管理
- Dockerfile
- 鏡像的分層
- add copy
- 構建實例
- 鏡像的導入導出
- 清理構建空間
- 配置阿里云加速器
- docker網絡模型
- 本地倉庫
- registry
- harbor
- IDEA部署docker
- 軟件安裝
- 安裝es
- 安裝MongoDB
- 安裝rabbitmq
- 安裝redis
- 安裝nacos
- 安裝mysql
- Minio
- 鏡像中心
- kubernetes
- 1. 安裝k8s
- 2.主要組件
- 3.污點
- 4.pod
- 5.控制器
- 6.網絡
- 7.探針
- 8.安裝Dashbord
- 9.secret
- 9.serviceAccount
- 10.service
- 資源清單
- kube-proxy
- flannel源文件
- 服務升級
- 筆記
- 鏡像
