## 掃描工具
### 常用掃描工具
~~~
Nmap
Masscan
masnmapscan
ZMap
御劍高速TCP端口掃描工具
御劍高速端口掃描工具
IISPutScanner
IISPutScanner增強版-DotNetScan v1.1 Beta
~~~
### 常用掃描工具使用
#### Nmap
項目地址:`https://github.com/nmap/nmap`
* 掃描多個IP
~~~
掃描整個子網 nmap 192.168.6.1/24
nmap 192.168.1.1/16
nmap 192.168.1-30.1-254
nmap 192.168.1-254.6
掃描多個主機 namp 192.168.6.2 192.168.6.6
掃描一個小范圍 nmap 192.168.6.2-10
掃描txt內的ip列表 nmap -iL text.txt
掃描除某個目標外 nmap 192.168.6.1/24 -exclude 192.168.6.25
~~~
* 繞過Firewalld掃描主機端口
通過不同的協議(TCP半連接、TCP全連接、ICMP、UDP等)的掃描繞過Firewalld的限制
~~~
nmap -sP 192.33.6.128
nmap -sT 192.33.6.128
nmap -sS 192.33.6.128
nmap -sU 192.33.6.128
nmap -sF 192.33.6.128
nmap -sX 192.33.6.128
nmap -sN 192.33.6.128
~~~
* 初步掃描端口信息
~~~
nmap -T4 -A -v -Pn 192.168.1.1/24 -p 21,22,23,25,80,81,82,83,88,110,143,443,445,512,513,514,1433,1521,2082,2083,2181,2601,2604,3128,3306,3389,3690,4848,5432,5900,5984,6379,7001,7002,8069,8080,8081,8086,8088,9200,9300,11211,10000,27017,27018,50000,50030,50070 -oN nmap_result.txt
~~~
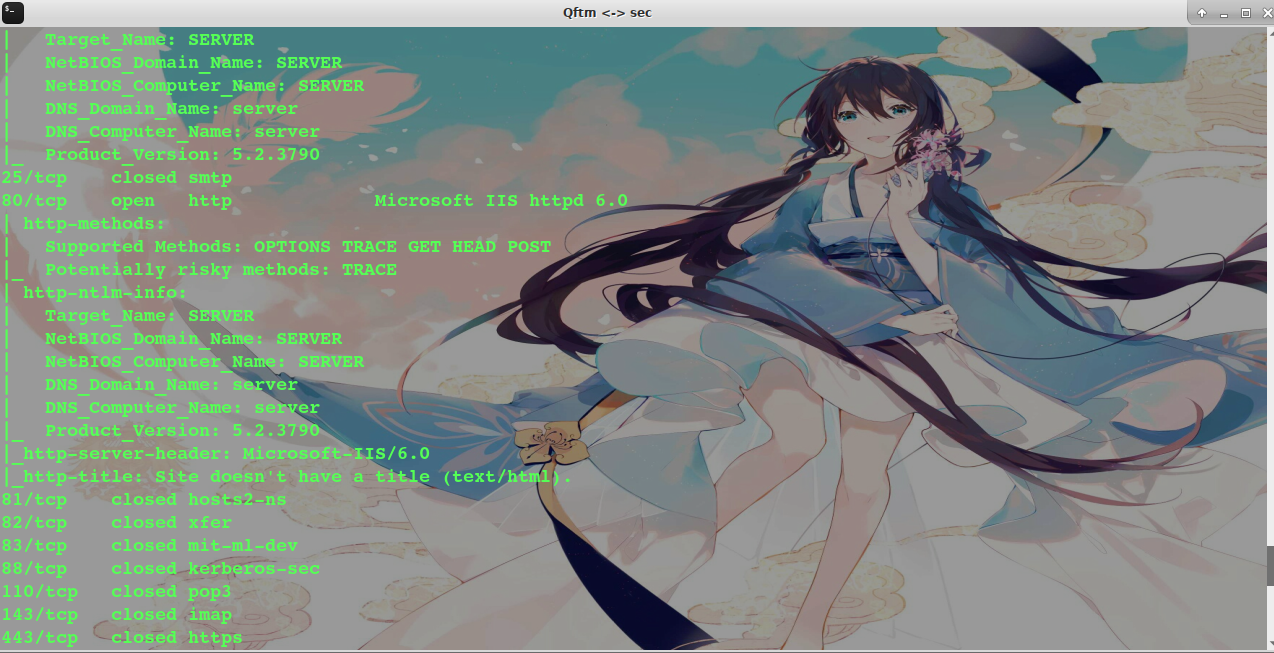
* 掃描端口并且標記可以爆破的服務
~~~
nmap 127.0.0.1 --script=ftp-brute,imap-brute,smtp-brute,pop3-brute,mongodb-brute,redis-brute,ms-sql-brute,rlogin-brute,rsync-brute,mysql-brute,pgsql-brute,oracle-sid-brute,oracle-brute,rtsp-url-brute,snmp-brute,svn-brute,telnet-brute,vnc-brute,xmpp-brute
~~~
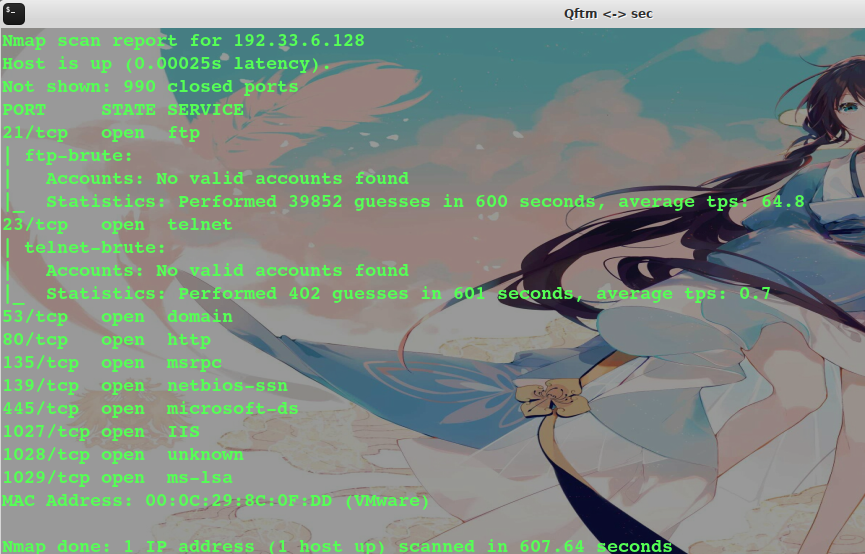
* 判斷常見的漏洞并掃描端口
~~~
nmap 127.0.0.1 --script=auth,vuln
~~~
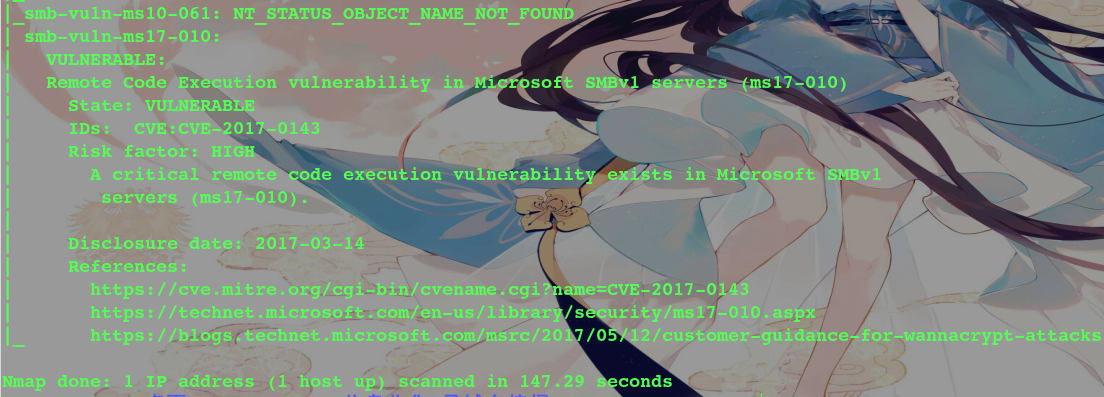
* 精確判斷漏洞并掃描端口
~~~
nmap 127.0.0.1 --script=dns-zone-transfer,ftp-anon,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221,http-backup-finder,http-cisco-anyconnect,http-iis-short-name-brute,http-put,http-php-version,http-shellshock,http-robots.txt,http-svn-enum,http-webdav-scan,iis-buffer-overflow,iax2-version,memcached-info,mongodb-info,msrpc-enum,ms-sql-info,mysql-info,nrpe-enum,pptp-version,redis-info,rpcinfo,samba-vuln-cve-2012-1182,smb-vuln-ms08-067,smb-vuln-ms17-010,snmp-info,sshv1,xmpp-info,tftp-enum,teamspeak2-version
~~~
#### Masscan
項目地址:`https://github.com/robertdavidgraham/masscan`
Masscan主要是真對全網進行端口掃描
#### Masscan+Nmap
有些時候網站的入口點屬于非常規端口,因此是必須要做全端口掃描,做全端口掃描的時候由于**namp**發包量大經常出現各種問題,如端口掃描不全、獲得信息不準等等,為了解決上述問題,這里提供一個**masscan+nmap**結合的方式進行快速掃描。
原理:使用masscan做全端口開放檢測,檢測出來端口信息后,用nmap進行服務信息識別。
使用:終端輸入以下命令執行即可
~~~
# masscan 192.33.6.145 -p1-65535 --rate 1000 -oL ports
# ports=$(cat ports | awk -F " " '{print $3}' | sort -n | tr '\n' ',' | sed 's/,$//' | sed 's/^,,//')
# nmap -sV -p $ports 192.33.6.145
~~~
#### masnmapscan
項目地址:`https://github.com/hellogoldsnakeman/masnmapscan-V1.0`
masnmapscan整合了masscan和nmap兩款掃描器,masscan掃描端口,nmap掃描端口對應服務,二者結合起來實現了又快又好地掃描。并且加入了針對目標資產有防火墻的應對措施。
#### Zmap
項目地址:`https://github.com/zmap/zmap`
Zmap主要是真對全網進行端口掃描
#### 御劍高速TCP端口掃描工具
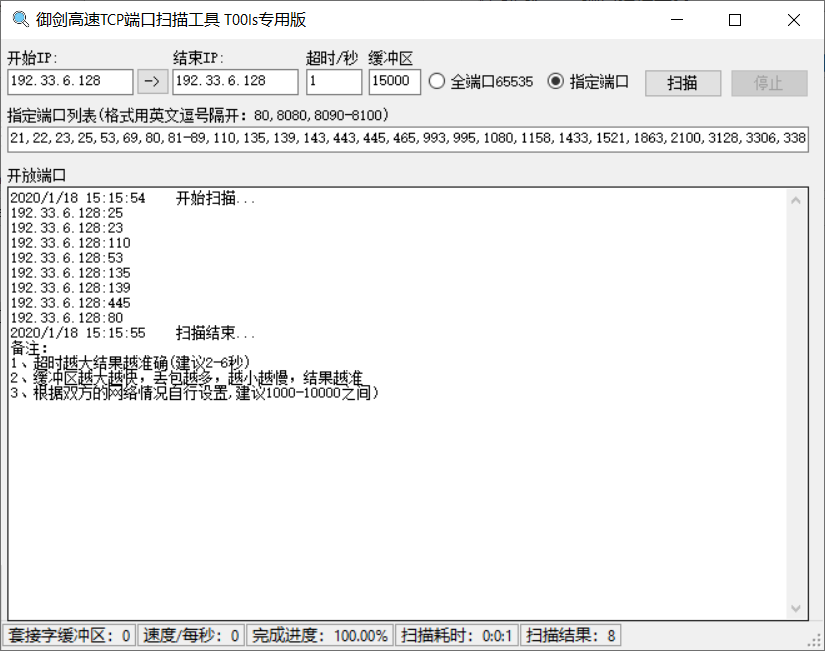
#### 御劍高速端口掃描工具
- src導航站
- kali和msf
- 信息收集
- 收集域名信息
- Whois 查詢
- 備案信息查詢
- 信用信息查詢
- IP反查站點的站
- 瀏覽器插件
- 收集子域名信息
- 在線平臺
- 工具枚舉
- ssl與證書透明度
- DNS歷史解析
- DNS域傳送漏洞
- C段探測
- JS文件域名&ip探測
- 搜索引擎&情報社區
- google黑客
- 威脅情報
- 鐘馗之眼
- 收集相關應用信息
- 微信公眾號&微博
- APP收集&反編譯
- 收集常用端口信息
- 常見端口&解析&總結
- 掃描工具
- 網絡空間引擎搜索
- 瀏覽器插件
- nmap掃描
- 收集敏感信息
- 源碼泄露
- 郵箱信息收集
- 備份文件泄露
- 目錄&后臺掃描
- 公網網盤
- 歷史資產
- 指紋&WAF&CDN識別
- 指紋識別
- CDN識別
- 繞過CDN查找真實IP
- WAF識別
- 漏洞資源和社工
- 漏洞公共資源庫
- 社會工程
- 資產梳理
- 各種對滲透有幫助的平臺
- 掃描器
- 掃描器對比
- AppScan(IBM)_web和系統
- AWVS_web掃描
- X-Scan_系統掃描
- WebInspect_HP_WEB
- Netsparker_web
- WVSS_綠盟_web
- 安恒明鑒
- Nessus_系統
- nexpose_系統
- 啟明天鏡_web_系統
- SQL注入
- 常用函數
- sql注入步驟
- union注入和information_schema庫
- 函數和報錯注入
- SQL盲注
- 其他注入方式
- 防止SQL注入解決方案
- Access數據庫注入
- MSSQL數據庫注入
- MYSQL數據庫注入
- 神器SQLmap
- xss跨站腳本攻擊
- xss原理和分類
- xss案例和修復
- xss繞過技巧
- xss案例
- 文件上傳下載包含
- 常有用文件路徑
- 文件上傳漏洞
- 文件下載漏洞
- 文件包含漏洞
- upload-labs上傳漏洞練習
- XXE、SSRF、CSRF
- SSRF原理基礎
- SSRF案例實戰
- CSRF原理基礎
- CSRF案例及防范
- XXE之XML_DTD基礎
- XXE之payload與修復
- XXE結合SSRF
- 遠程命令執行與反序列化
- 遠程命令和代碼執行漏洞
- 反序列化漏洞
- 驗證碼與暴力破解
- 爆破與驗證碼原理
- CS架構暴力破解
- BS架構暴力破解
- WEB編輯器漏洞
- 編輯器漏洞基礎
- Ewebeditor編輯器
- FCKeditor編輯器
- 其他編輯器
- web中間件漏洞
- 中間件解析漏洞
- Tomcat常見的漏洞總結
- Jboss漏洞利用總結
- Weblogic漏洞利用總結
- WEB具體步驟
- 旁注和越權
- CDN繞過
- 越權與邏輯漏洞
- WEB應用常見其他漏洞
- WEB登陸頁面滲透思路
- 獲取WEBshell思路
- 社工、釣魚、apt
- 社工和信息收集
- 域名欺騙
- 釣魚郵件
- 一些釣魚用的掛馬工具
- 代碼審計
- 代碼審計工具
- WAF繞過
- WAF基礎及云WAF
- 各種WAF繞過方法
- 繞過WAF上傳文件
- 系統提權
- windows系統提權
- linux系統提權
- 數據庫提權操作系統
- 內網橫向滲透
- 內網穿透方式
- 一些內網第三方應用提權
- ARP與DOS
- ARP欺騙
- DOS與DDOS
- 一些DOS工具
