### 1、部署nginx
我們需要在hdss7-11,hdss7-12 這兩個機器做192.168.206.70虛擬VIP (keepalived)??,來反向代理hdss-73??hdss-74 hdss-75 apiserver的L4 4層 6443,保證了6443端口的高可用。
nginx部署和配置
yum install nginx -y
#### nginx四層負載,必須與http同級:
```
vi /etc/nginx/nginx.conf
stream {
upstream kube-apiserver {
server 10.4.7.21:6443 max_fails=3 fail_timeout=30s;
server 10.4.7.22:6443 max_fails=3 fail_timeout=30s;
}
server {
listen 7443;
proxy_connect_timeout 2s;
proxy_timeout 900s;
proxy_pass kube-apiserver;
}
}
```
#### 啟動nginx
```
nginx -t
systemctl start nginx
systemctl enable nginx
```
### 2、部署keepalived配置
#### 安裝的機器hdss7-11,hdss7-12
```
[root@hdss-71 ~]# yum install -y keepalived
```
### 配置監聽7443端口的檢查腳本
```
vi /etc/keepalived/check_port.sh
#!/bin/bash
#keepalived 監控端口腳本
#使用方法:
#在keepalived的配置文件中
#vrrp_script check_port {#創建一個vrrp_script腳本,檢查配置
# script "/etc/keepalived/check_port.sh 6379" #配置監聽的端口
# interval 2 #檢查腳本的頻率,單位(秒)
#}
CHK_PORT=$1
if [ -n "$CHK_PORT" ];then
PORT_PROCESS=`ss -lnt|grep $CHK_PORT|wc -l`
if [ $PORT_PROCESS -eq 0 ];then
echo "Port $CHK_PORT Is Not Used,End."
exit 1
fi
else
echo "Check Port Cant Be Empty!"
fi
```
#### 監聽腳本授權
```
chmod +x /etc/keepalived/check_port.sh
```
#### 編輯keepalived配置文件,注意主從配置文件不一樣:
hdss7-11 主:
vi /etc/keepalived/keepalived.conf
```
! Configuration File for keepalived
global_defs {
router_id 10.4.7.11
}
vrrp_script chk_nginx {
script "/etc/keepalived/check_port.sh 7443"
interval 2
weight -20
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 251
priority 100
advert_int 1
mcast_src_ip 10.4.7.11
nopreempt #非搶占式 ,當主節點掛了以后,從節點vip飄到從上,主節點恢復以后,不主動飄回主,需要手動重啟keepalived
authentication {
auth_type PASS
auth_pass 11111111
}
track_script {
chk_nginx
}
virtual_ipaddress {
10.4.7.10
}
}
```
解釋:
? router\_id 192.168.206.71??
? ? vrrp\_script chk\_nginx { ???????????????腳本弄進來
????script "/etc/keepalived/check\_port.sh 7443"????傳參7443
????interface ens33???網卡
hdss7-12 從
```
! Configuration File for keepalived
global_defs {
router_id 10.4.7.12
}
vrrp_script chk_nginx {
script "/etc/keepalived/check_port.sh 7443"
interval 2
weight -20
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 251
mcast_src_ip 10.4.7.12
priority 90
advert_int 1
authentication {
auth_type PASS
auth_pass 11111111
}
track_script {
chk_nginx
}
virtual_ipaddress {
10.4.7.10
}
}
```
#### 啟動keepalived
```
systemctl start keepalived
systemctl enable keepalived
```
#### 查看情況
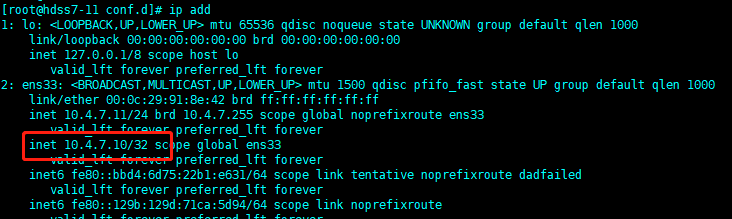
?如果keepalived出現腦裂問題,兩臺上面都有vip,可以加入以下配置,將多播修改成單播:
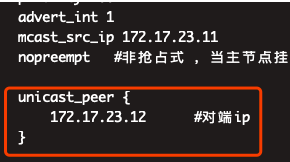
**注意:**
**主節點中,必須加上 nopreempt??非搶占式
因為一旦因為網絡抖動導致keepalived未檢測到主節點7443端口。就會觸發VIP漂移,這樣從節點就會接管,由于網絡抖動keepalived檢測主節點7443,會立馬恢復到主節點,這算是重大的責任不能讓它自動飄回來,所以必須配置 nopreempt:非搶占式,達到飄逸從節點后,即使檢測主節點7443,也不會遷移VIP到主節點,必須要分析原因后手動遷移VIP到主節點!如主節點確認正常后,重啟備節點的keepalive,讓VIP飄到主節點.**
- 空白目錄
- k8s
- k8s介紹和架構圖
- 硬件環境和準備工作
- bind9-DNS服務部署
- 私有倉庫harbor部署
- k8s-etcd部署
- api-server部署
- 配置apiserver L4代理
- controller-manager部署
- kube-scheduler部署
- node節點kubelet 部署
- node節點kube-proxy部署
- cfss-certinfo使用
- k8s網絡-Flannel部署
- k8s網絡優化
- CoreDNS部署
- k8s服務暴露之ingress
- 常用命令記錄
- k8s-部署dashboard服務
- K8S平滑升級
- k8s服務交付
- k8s交付dubbo服務
- 服務架構圖
- zookeeper服務部署
- Jenkins服務+共享存儲nfs部署
- 安裝配置maven和java運行時環境的底包鏡像
- 使用blue ocean流水線構建鏡像
- K8S生態--交付prometheus監控
- 介紹
- 部署4個exporter
- 部署prometheus server
- 部署grafana
- alert告警部署
- 日志收集ELK
- 制作Tomcat鏡像
- 部署ElasticSearch
- 部署kafka和kafka-manager
- filebeat鏡像制作
- 部署logstash
- 部署Kibana
- Apollo交付到Kubernetes集群
- Apollo簡介
- 交付apollo-configservice
- 交付apollo-adminservice
- 交付apollo-portal
- k8s-CICD
- 集群整體架構
- 集群安裝
- harbor倉庫和nfs部署
- nginx-ingress-controller服務部署
- gitlab服務部署
- gitlab服務優化
- gitlab-runner部署
- dind服務部署
- CICD自動化服務devops演示
- k8s上服務日志收集
