k8s的GUI資源管理插件-儀表盤
部署kubernetes-dashboard
1、鏡像準備
```
docker pull k8scn/kubernetes-dashboard-amd64:v1.8.3
docker images | grep dashboard
docker tag fcac9aa03fd6 harbor.od.com/public/dashboard:v1.8.3
docker push harbor.od.com/public/dashboard:v1.8.3
```
準備資源清單
https://github.com/kubernetes/kubernetes/blob/master/cluster/addons/dashboard/dashboard.yaml
創建目錄
```
mkdir /data/k8s-yaml/dashboard
cd /data/k8s-yaml/dashboard/
```
[root@hdss7-200 dashboard]# cat rbac.yaml
```
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
```
[root@hdss7-200 dashboard]# cat dp.yaml
```
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.10.1
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
```
[root@hdss7-200 dashboard]# cat svc.yaml
```
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
```
[root@hdss7-200 dashboard]# cat ingress.yaml
```
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
```
創建資源:任意node
```
kubectl create -f http://k8s-yaml.od.com/dashboard/rbac.yaml
kubectl create -f http://k8s-yaml.od.com/dashboard/dp.yaml
kubectl create -f http://k8s-yaml.od.com/dashboard/svc.yaml
kubectl create -f http://k8s-yaml.od.com/dashboard/ingress.yaml
```
添加域名解析:
```
vi /var/named/od.com.zone
dashboard A 10.4.7.10
systemctl restart named
```
通過瀏覽器訪問:
http://dashboard.od.com
但是,我們可以看到我們安裝1.8版本的dashboard,默認是可以跳過驗證的:

很顯然,跳過登錄,是不科學的,因為我們在配置dashboard的rbac權限時,綁定的角色是system:admin,這個是集群管理員的角色,權限很大,所以這里我們把版本換成1.10以上版本
下載1.10.1版本:
```
docker pull loveone/kubernetes-dashboard-amd64:v1.10.1
docker tag f9aed6605b81 harbor.od.com/public/dashboard:v1.10.1
docker push harbor.od.com/public/dashboard:v1.10.1
```
修改dp.yaml重新應用,我直接用edit修改了,沒有使用apply
kubectl edit deploy kubernetes-dashboard -n kube-system

?可以看到這里原來的skip跳過已經沒有了,我們如果想登陸,必須輸入token,那我們如何獲取token呢:
kubectl get secret -n kube-system
kubectl describe secret kubernetes-dashboard-admin-token-pg77n -n kube-system
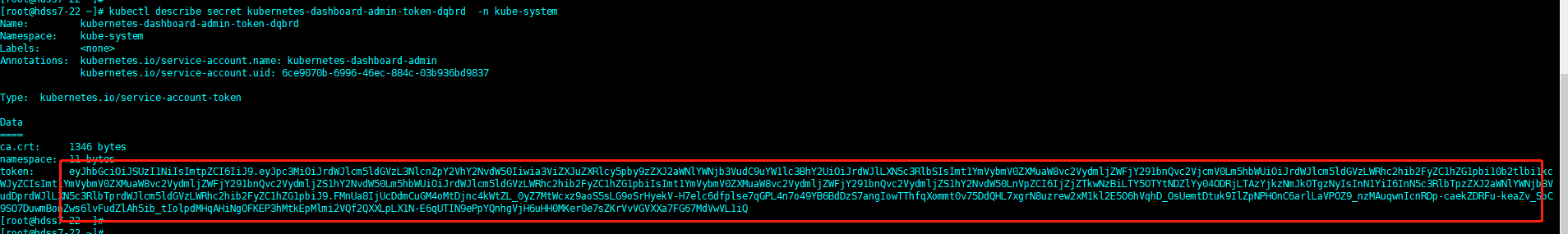
這樣我們就拿到了token,接下來我們試試能不能登錄:
我們發現我們還是無法登錄,原因是必須使用https登錄,接下來我們需要申請證書:
接下來我們申請證書:
依然使用cfssl來申請證書:hdss7-200
cd /opt/certs/
vi dashboard-csr.json
```
{
"CN": "*.od.com",
"hosts": [
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
]
}
```
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=server dashboard-csr.json |cfssl-json -bare dashboard
然后拷貝到我們nginx的服務器上:7-11 7-12 都需要
cd /etc/nginx/
mkdir certs
cd certs
scp hdss7-200:/opt/cert/dash* ./
cd /etc/nginx/conf.d/
vi dashboard.od.com.conf
```
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.pem";
ssl_certificate_key "certs/dashboard-key.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
```
nginx -t
nginx -s reload
dashboard圖形監控 heapster部署
```
docker pull quay.io/bitnami/heapster:1.5.4
docker tag c359b95ad38b harbor.od.com/public/heapster:v1.5.4
docker push harbor.od.com/public/heapster:v1.5.4
```
[root@hdss7-200 heapster]# cat rbac.yaml
```
apiVersion: v1
kind: ServiceAccount
metadata:
name: heapster
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: heapster
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:heapster
subjects:
- kind: ServiceAccount
name: heapster
namespace: kube-system
```
[root@hdss7-200 heapster]# cat dp.yaml
```
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: heapster
namespace: kube-system
spec:
replicas: 1
template:
metadata:
labels:
task: monitoring
k8s-app: heapster
spec:
serviceAccountName: heapster
containers:
- name: heapster
image: harbor.od.com/public/heapster:v1.5.4
imagePullPolicy: IfNotPresent
command:
- /opt/bitnami/heapster/bin/heapster
- --source=kubernetes:https://kubernetes.default
```
[root@hdss7-200 heapster]# cat svc.yaml
```
apiVersion: v1
kind: Service
metadata:
labels:
task: monitoring
# For use as a Cluster add-on (https://github.com/kubernetes/kubernetes/tree/master/cluster/addons)
# If you are NOT using this as an addon, you should comment out this line.
kubernetes.io/cluster-service: 'true'
kubernetes.io/name: Heapster
name: heapster
namespace: kube-system
spec:
ports:
- port: 80
targetPort: 8082
selector:
k8s-app: heapster
```

- 空白目錄
- k8s
- k8s介紹和架構圖
- 硬件環境和準備工作
- bind9-DNS服務部署
- 私有倉庫harbor部署
- k8s-etcd部署
- api-server部署
- 配置apiserver L4代理
- controller-manager部署
- kube-scheduler部署
- node節點kubelet 部署
- node節點kube-proxy部署
- cfss-certinfo使用
- k8s網絡-Flannel部署
- k8s網絡優化
- CoreDNS部署
- k8s服務暴露之ingress
- 常用命令記錄
- k8s-部署dashboard服務
- K8S平滑升級
- k8s服務交付
- k8s交付dubbo服務
- 服務架構圖
- zookeeper服務部署
- Jenkins服務+共享存儲nfs部署
- 安裝配置maven和java運行時環境的底包鏡像
- 使用blue ocean流水線構建鏡像
- K8S生態--交付prometheus監控
- 介紹
- 部署4個exporter
- 部署prometheus server
- 部署grafana
- alert告警部署
- 日志收集ELK
- 制作Tomcat鏡像
- 部署ElasticSearch
- 部署kafka和kafka-manager
- filebeat鏡像制作
- 部署logstash
- 部署Kibana
- Apollo交付到Kubernetes集群
- Apollo簡介
- 交付apollo-configservice
- 交付apollo-adminservice
- 交付apollo-portal
- k8s-CICD
- 集群整體架構
- 集群安裝
- harbor倉庫和nfs部署
- nginx-ingress-controller服務部署
- gitlab服務部署
- gitlab服務優化
- gitlab-runner部署
- dind服務部署
- CICD自動化服務devops演示
- k8s上服務日志收集
