# Static Application Security Testing (SAST)
> 原文:[https://docs.gitlab.com/ee/user/application_security/sast/](https://docs.gitlab.com/ee/user/application_security/sast/)
* [Overview](#overview)
* [Use cases](#use-cases)
* [Requirements](#requirements)
* [Supported languages and frameworks](#supported-languages-and-frameworks)
* [Making SAST analyzers available to all GitLab tiers](#making-sast-analyzers-available-to-all-gitlab-tiers)
* [Summary of features per tier](#summary-of-features-per-tier)
* [Contribute your scanner](#contribute-your-scanner)
* [Configuration](#configuration)
* [Customizing the SAST settings](#customizing-the-sast-settings)
* [Overriding SAST jobs](#overriding-sast-jobs)
* [Using environment variables to pass credentials for private repositories](#using-environment-variables-to-pass-credentials-for-private-repositories)
* [Using a variable to pass username and password to a private Maven repository](#using-a-variable-to-pass-username-and-password-to-a-private-maven-repository)
* [Enabling Docker-in-Docker](#enabling-docker-in-docker)
* [Enabling Kubesec analyzer](#enabling-kubesec-analyzer)
* [Pre-compilation](#pre-compilation)
* [Available variables](#available-variables)
* [Logging Level](#logging-level)
* [Custom Certificate Authority](#custom-certificate-authority)
* [Docker images](#docker-images)
* [Vulnerability filters](#vulnerability-filters)
* [Docker-in-Docker orchestrator](#docker-in-docker-orchestrator)
* [Analyzer settings](#analyzer-settings)
* [Custom environment variables](#custom-environment-variables)
* [Reports JSON format](#reports-json-format)
* [Secret detection](#secret-detection)
* [Security Dashboard](#security-dashboard)
* [Interacting with the vulnerabilities](#interacting-with-the-vulnerabilities)
* [Vulnerabilities database](#vulnerabilities-database)
* [Vulnerabilities database update](#vulnerabilities-database-update)
* [Running SAST in an offline environment](#running-sast-in-an-offline-environment)
* [Requirements for offline SAST](#requirements-for-offline-sast)
* [Make GitLab SAST analyzer images available inside your Docker registry](#make-gitlab-sast-analyzer-images-available-inside-your-docker-registry)
* [Set SAST CI job variables to use local SAST analyzers](#set-sast-ci-job-variables-to-use-local-sast-analyzers)
* [Troubleshooting](#troubleshooting)
* [`Error response from daemon: error processing tar file: docker-tar: relocation error`](#error-response-from-daemon-error-processing-tar-file-docker-tar-relocation-error)
# Static Application Security Testing (SAST)[](#static-application-security-testing-sast-ultimate "Permalink")
[Introduced](https://gitlab.com/gitlab-org/gitlab/-/issues/3775) in [GitLab Ultimate](https://about.gitlab.com/pricing/) 10.3.
**注意:**白皮書["應用程序安全性發生](https://about.gitlab.com/resources/whitepaper-seismic-shift-application-security/)了[地震變化"](https://about.gitlab.com/resources/whitepaper-seismic-shift-application-security/)說明**了前 6 種攻擊中有 4 種是基于應用程序的** . 下載它以了解如何保護您的組織.
## Overview[](#overview "Permalink")
如果您使用的是[GitLab CI / CD](../../../ci/README.html) ,則可以使用靜態應用程序安全性測試(SAST)分析源代碼中的已知漏洞.
您可以通過執行以下任一操作來利用 SAST:
* 在現有的`.gitlab-ci.yml`文件中[包括 SAST 模板](#configuration) .
* 隱式使用[Auto DevOps](../../../topics/autodevops/stages.html#auto-sast-ultimate)提供的[Auto](../../../topics/autodevops/index.html) [SAST](../../../topics/autodevops/stages.html#auto-sast-ultimate) .
GitLab 檢查 SAST 報告,比較發現的源分支和目標分支之間的漏洞,并在合并請求中顯示信息.
[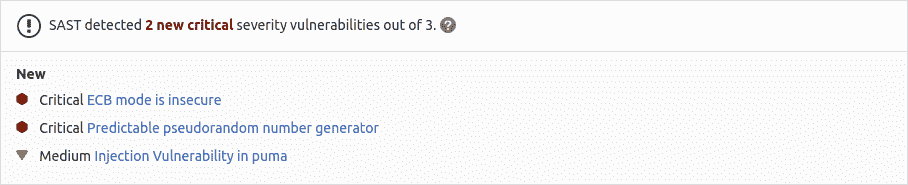](img/sast_v13_2.png)
結果按漏洞的優先級排序:
1. Critical
2. High
3. Medium
4. Low
5. Unknown
6. 其他一切
**注意:**管道包含多個作業,包括 SAST 和 DAST 掃描. 如果任何作業由于任何原因未能完成,則安全信息中心將不會顯示 SAST 掃描儀輸出. 例如,如果 SAST 作業完成但 DAST 作業失敗,則安全性儀表板將不會顯示 SAST 結果. 分析器將在失敗時輸出[退出代碼](../../../development/integrations/secure.html#exit-code) .
## Use cases[](#use-cases "Permalink")
* 您的代碼在類中具有潛在的危險屬性,或者不安全的代碼可能導致意外的代碼執行.
* 您的應用程序容易受到跨站點腳本(XSS)攻擊的攻擊,這些攻擊可用于未經授權訪問會話數據.
## Requirements[](#requirements "Permalink")
要運行 SAST 工作,默認情況下,你需要 GitLab 亞軍與[`docker`](https://docs.gitlab.com/runner/executors/docker.html)或[`kubernetes`](https://docs.gitlab.com/runner/install/kubernetes.html)執行. 如果您在 GitLab.com 上使用共享的 Runners,則默認啟用該功能.
從 GitLab 13.0 開始,僅當您已[為 SAST 啟用 Docker-in-Docker 時,才](#enabling-docker-in-docker)需要 Docker 特權模式.
**警告:**目前,我們的 SAST 作業需要 Linux 容器類型. Windows 容器尚不支持.**注意:**如果使用自己的 Runners,請確保安裝的 Docker 版本**不是** `19.03.0` . 有關詳細[信息](#error-response-from-daemon-error-processing-tar-file-docker-tar-relocation-error) ,請參見[故障排除信息](#error-response-from-daemon-error-processing-tar-file-docker-tar-relocation-error) .
## Supported languages and frameworks[](#supported-languages-and-frameworks "Permalink")
下表顯示了支持的語言,程序包管理器和框架以及使用了哪些工具.
| 語言(包管理器)/框架 | 掃描工具 | 在 GitLab 版本中引入 |
| --- | --- | --- |
| .NET Core | [Security Code Scan](https://security-code-scan.github.io) | 11.0 |
| .NET Framework | [Security Code Scan](https://security-code-scan.github.io) | 13.0 |
| Any | [Gitleaks](https://github.com/zricethezav/gitleaks) and [TruffleHog](https://github.com/dxa4481/truffleHog) | 11.9 |
| Apex(Salesforce) | [PMD](https://pmd.github.io/pmd/index.html) | 12.1 |
| C/C++ | [Flawfinder](https://github.com/david-a-wheeler/flawfinder) | 10.7 |
| 長生不老藥(鳳凰城) | [Sobelow](https://github.com/nccgroup/sobelow) | 11.10 |
| Go | [Gosec](https://github.com/securego/gosec) | 10.7 |
| Groovy( [Ant](https://ant.apache.org/) , [Gradle](https://s0gradle0org.icopy.site/) , [Maven](https://maven.apache.org/)和[SBT](https://www.scala-sbt.org/) ) | 帶有[find-sec-bugs](https://find-sec-bugs.github.io/)插件的[SpotBugs](https://spotbugs.github.io/) | 11.3(Gradle)和 11.9(Ant,Maven,SBT) |
| 頭盔圖 | [Kubesec](https://github.com/controlplaneio/kubesec) | 13.1 |
| Java( [Ant](https://ant.apache.org/) , [Gradle](https://s0gradle0org.icopy.site/) , [Maven](https://maven.apache.org/)和[SBT](https://www.scala-sbt.org/) ) | 帶有[find-sec-bugs](https://find-sec-bugs.github.io/)插件的[SpotBugs](https://spotbugs.github.io/) | 10.6(Maven),10.8(Grade)和 11.9(Ant,SBT) |
| JavaScript | [ESLint security plugin](https://github.com/nodesecurity/eslint-plugin-security) | 11.8,在 13.2 中移至[GitLab Core](https://about.gitlab.com/pricing/) |
| 州長宣言 | [Kubesec](https://github.com/controlplaneio/kubesec) | 12.6 |
| Node.js | [NodeJsScan](https://github.com/ajinabraham/NodeJsScan) | 11.1 |
| PHP | [phpcs-security-audit](https://github.com/FloeDesignTechnologies/phpcs-security-audit) | 10.8 |
| Python( [點子](https://pip.pypa.io/en/stable/) ) | [bandit](https://github.com/PyCQA/bandit) | 10.3 |
| React | [ESLint react plugin](https://github.com/yannickcr/eslint-plugin-react) | 12.5 |
| Ruby on Rails | [brakeman](https://brakemanscanner.org) | 10.3,于 13.1 中移至[GitLab Core](https://about.gitlab.com/pricing/) |
| Scala( [Ant](https://ant.apache.org/) , [Gradle](https://s0gradle0org.icopy.site/) , [Maven](https://maven.apache.org/)和[SBT](https://www.scala-sbt.org/) ) | 帶有[find-sec-bugs](https://find-sec-bugs.github.io/)插件的[SpotBugs](https://spotbugs.github.io/) | 11.0(SBT)和 11.9(Ant,Gradle,Maven) |
| TypeScript | [ESLint security plugin](https://github.com/nodesecurity/eslint-plugin-security) | 11.9,在 13.2 中與 ESLint 合并 |
**注意:** Java 分析器還可以用于[Gradle 包裝器](https://s0docs0gradle0org.icopy.site/current/userguide/gradle_wrapper.html) , [Grails](https://grails.org/)和[Maven 包裝器](https://github.com/takari/maven-wrapper)等變體.
### Making SAST analyzers available to all GitLab tiers[](#making-sast-analyzers-available-to-all-gitlab-tiers "Permalink")
所有開放源代碼(OSS)分析器都正在接受審核,并有可能移至 GitLab 核心層. 可以在相應的[史詩中](https://gitlab.com/groups/gitlab-org/-/epics/2098)跟蹤進度.
請注意,對[Docker-in-Docker 的](#enabling-docker-in-docker)支持不會擴展到 GitLab 核心層.
#### Summary of features per tier[](#summary-of-features-per-tier "Permalink")
下表列出了在不同的[GitLab 層](https://about.gitlab.com/pricing/)中可用的不同功能:
| Capability | 在核心 | 終極 |
| --- | --- | --- |
| [Configure SAST Scanners](#configuration) | | |
| [Customize SAST Settings](#customizing-the-sast-settings) | | |
| View [JSON Report](#reports-json-format) | | |
| [Presentation of JSON Report in Merge Request](#overview) | | |
| [Interaction with Vulnerabilities](#interacting-with-the-vulnerabilities) | | |
| [Access to Security Dashboard](#security-dashboard) | | |
## Contribute your scanner[](#contribute-your-scanner "Permalink")
[安全掃描程序集成](../../../development/integrations/secure.html)文檔說明了如何將其他安全掃描[程序集成](../../../development/integrations/secure.html)到 GitLab 中.
## Configuration[](#configuration "Permalink")
**注意:**如果您使用的是[Auto DevOps](../../../topics/autodevops/index.html)提供的[Auto](../../../topics/autodevops/index.html) [SAST,則不必](../../../topics/autodevops/stages.html#auto-sast-ultimate)按照本節中的說明手動配置 SAST.
對于 GitLab 11.9 和更高版本,要啟用 SAST,您必須[包括](../../../ci/yaml/README.html#includetemplate)作為 GitLab 安裝的一部分提供的[`SAST.gitlab-ci.yml`模板](https://gitlab.com/gitlab-org/gitlab/blob/master/lib/gitlab/ci/templates/Security/SAST.gitlab-ci.yml) . 對于 11.9 之前的 GitLab 版本,您可以復制和使用該模板中定義的作業.
將以下內容添加到您的`.gitlab-ci.yml`文件中:
```
include:
- template: SAST.gitlab-ci.yml
```
隨附的模板將在 CI / CD 管道中創建 SAST 作業,并掃描項目的源代碼以查找可能的漏洞.
結果將保存為[SAST 報告工件](../../../ci/pipelines/job_artifacts.html#artifactsreportssast-ultimate) ,您可以稍后下載和分析. 由于實施限制,我們始終采用最新的 SAST 工件.
### Customizing the SAST settings[](#customizing-the-sast-settings "Permalink")
可以使用`.gitlab-ci.yml`的[`variables`](../../../ci/yaml/README.html#variables)參數通過[環境變量](#available-variables)更改 SAST 設置. 在下面的示例中,我們包括 SAST 模板,同時將`SAST_GOSEC_LEVEL`變量設置為`2` :
```
include:
- template: SAST.gitlab-ci.yml
variables:
SAST_GOSEC_LEVEL: 2
```
因為模板是[在](../../../ci/yaml/README.html#include)管道配置[之前進行評估](../../../ci/yaml/README.html#include)的,所以最后提到的變量優先.
### Overriding SAST jobs[](#overriding-sast-jobs "Permalink")
**棄用:**從 GitLab 13.0 開始,不再支持[`only`和`except`](../../../ci/yaml/README.html#onlyexcept-basic)的使用. 覆蓋模板時,必須使用[`rules`](../../../ci/yaml/README.html#rules) .
要覆蓋作業定義(例如,更改`variables`或`dependencies`類的屬性),請聲明與要覆蓋的 SAST 作業同名的作業. 將此新作業放置在包含模板之后,并在其下指定其他任何鍵. 例如,這使得能夠`FAIL_NEVER`為`spotbugs`分析器:
```
include:
- template: SAST.gitlab-ci.yml
spotbugs-sast:
variables:
FAIL_NEVER: 1
```
### Using environment variables to pass credentials for private repositories[](#using-environment-variables-to-pass-credentials-for-private-repositories "Permalink")
一些分析器需要下載項目的依賴項才能執行分析. 反過來,此類依賴項可能存在于私有 Git 存儲庫中,因此需要諸如用戶名和密碼之類的憑據才能下載它們. 根據分析器的不同,可以通過[自定義環境變量](#custom-environment-variables)向其提供此類憑據.
#### Using a variable to pass username and password to a private Maven repository[](#using-a-variable-to-pass-username-and-password-to-a-private-maven-repository "Permalink")
如果您的私有 Maven 存儲庫需要登錄憑據,則可以使用`MAVEN_CLI_OPTS`環境變量.
閱讀有關[如何使用私有 Maven 存儲庫的](../index.html#using-private-maven-repos)更多[信息](../index.html#using-private-maven-repos) .
### Enabling Docker-in-Docker[](#enabling-docker-in-docker "Permalink")
如果需要,您可以啟用 Docker-in-Docker 來還原 GitLab 13.0 之前存在的 SAST 行為. 請按照以下步驟操作:
1. 在[特權模式下](https://docs.gitlab.com/runner/executors/docker.html)使用 Docker-inDocker 配置 GitLab Runner.
2. 將變量`SAST_DISABLE_DIND`設置為`false` :
```
include:
- template: SAST.gitlab-ci.yml
variables:
SAST_DISABLE_DIND: "false"
```
這將創建一個單一的`sast`在你的 CI / CD 管道,而不是多個作業`<analyzer-name>-sast`工作.
#### Enabling Kubesec analyzer[](#enabling-kubesec-analyzer "Permalink")
在 GitLab Ultimate 12.6 中[引入](https://gitlab.com/gitlab-org/gitlab/-/issues/12752) .
您需要將`SCAN_KUBERNETES_MANIFESTS`設置為`"true"`才能啟用 Kubesec 分析器. 在`.gitlab-ci.yml` ,定義:
```
include:
- template: SAST.gitlab-ci.yml
variables:
SCAN_KUBERNETES_MANIFESTS: "true"
```
#### Pre-compilation[](#pre-compilation "Permalink")
如果您的項目需要自定義構建配置,則最好避免在 SAST 執行期間進行編譯,而應將管道中較早階段的所有作業工件傳遞出去. 當需要執行`before_script`來準備掃描作業時,這是當前的策略.
要將項目的依賴項作為工件傳遞,這些依賴項必須包含在項目的工作目錄中,并使用`artifacts:path`配置進行指定. 如果存在所有依賴項,則可以將`COMPILE=false`變量提供給分析器,并且將跳過編譯:
```
image: maven:3.6-jdk-8-alpine
stages:
- build
- test
include:
- template: SAST.gitlab-ci.yml
build:
stage: build
script:
- mvn package -Dmaven.repo.local=./.m2/repository
artifacts:
paths:
- .m2/
- target/
spotbugs-sast:
dependencies:
- build
variables:
MAVEN_REPO_PATH: ./.m2/repository
COMPILE: false
artifacts:
reports:
sast: gl-sast-report.json
```
**注意:**必須顯式指定供應商目錄的路徑,以允許分析器識別已編譯的工件. 每個分析器的配置可能有所不同,但在上述 Java 的情況下,可以使用`MAVEN_REPO_PATH` . 有關可用選項的完整列表,請參見[分析器設置](#analyzer-settings) .
### Available variables[](#available-variables "Permalink")
可以使用環境變量[配置](#customizing-the-sast-settings) SAST.
#### Logging Level[](#logging-level "Permalink")
您可以通過設置`SECURE_LOG_LEVEL` env var 來控制日志的詳細程度. 默認設置為`info` ,您可以將其設置為以下任意級別:
* `fatal`
* `error`
* `warn`
* `info`
* `debug`
#### Custom Certificate Authority[](#custom-certificate-authority "Permalink")
要信任自定義證書頒發機構,請將`ADDITIONAL_CA_CERT_BUNDLE`變量設置為要在 SAST 環境中信任的 CA 證書包.
#### Docker images[](#docker-images "Permalink")
以下是與 Docker 映像相關的變量.
| Environment variable | Description |
| --- | --- |
| `SECURE_ANALYZERS_PREFIX` | 覆蓋提供默認映像(代理)的 Docker 注冊表名稱. 閱讀有關[自定義分析器的](analyzers.html)更多信息. |
| `SAST_ANALYZER_IMAGE_TAG` | **已棄用:**覆蓋默認映像的 Docker 標簽. 閱讀有關[自定義分析器的](analyzers.html)更多信息. |
| `SAST_DEFAULT_ANALYZERS` | 覆蓋默認圖像的名稱. 閱讀有關[自定義分析器的](analyzers.html)更多信息. |
| `SAST_DISABLE_DIND` | 禁用 Docker-in-Docker 并[單獨](#enabling-docker-in-docker)運行分析器. 默認情況下,此變量為`true` . |
#### Vulnerability filters[](#vulnerability-filters "Permalink")
一些分析器可以過濾掉給定閾值以下的漏洞.
| 環境變量 | 默認值 | Description |
| --- | --- | --- |
| `SAST_EXCLUDED_PATHS` | `spec, test, tests, tmp` | 根據路徑從輸出中排除漏洞. 這是逗號分隔的模式列表. 模式可以是全局變量,也可以是文件或文件夾路徑(例如`doc,spec` ). 父目錄也將匹配模式. |
| `SAST_BANDIT_EXCLUDED_PATHS` | ? | 逗號分隔的路徑列表,可從掃描中排除. 使用 Python 的[`fnmatch`語法](https://s0docs0python0org.icopy.site/2/library/fnmatch.html) ; 例如: `'*/tests/*, */venv/*'` |
| `SAST_BRAKEMAN_LEVEL` | 1 | 在給定的置信度下忽略 Brakeman 漏洞. 整數,1 =低 3 =高. |
| `SAST_DISABLE_BABEL` | `false` | 禁用 NodeJsScan 掃描儀的 Babel 處理. 設置為`true`將禁用 Babel 處理. 在 GitLab 13.2 中[引入](https://gitlab.com/gitlab-org/gitlab/-/issues/33065) . |
| `SAST_FLAWFINDER_LEVEL` | 1 | 在給定風險級別下忽略 Flawfinder 漏洞. 整數,0 =無風險,5 =高風險. |
| `SAST_GITLEAKS_ENTROPY_LEVEL` | 8.0 | 秘密檢測的最小熵. 浮動,0.0 =低,8.0 =高. |
| `SAST_GOSEC_LEVEL` | 0 | 在給定的置信度下忽略 Gosec 漏洞. 整數,0 =未定義,1 =低,2 =中,3 =高. |
| `SAST_GITLEAKS_COMMIT_FROM` | ? | 提交 Gitleaks 掃描始于. |
| `SAST_GITLEAKS_COMMIT_TO` | ? | Gitleaks 掃描的提交結束于. |
| `SAST_GITLEAKS_HISTORIC_SCAN` | `false` | 標記以啟用歷史性的 Gitleaks 掃描. |
#### Docker-in-Docker orchestrator[](#docker-in-docker-orchestrator "Permalink")
以下變量配置 Docker-in-Docker 協調器,因此僅在[啟用](#enabling-docker-in-docker) Docker-in-Docker 模式時才使用.
| 環境變量 | 默認值 | Description |
| --- | --- | --- |
| `SAST_ANALYZER_IMAGES` | ? | 以逗號分隔的自定義圖像列表. 默認圖像仍處于啟用狀態. 閱讀有關[自定義分析器的](analyzers.html)更多信息. |
| `SAST_PULL_ANALYZER_IMAGES` | 1 | 從 Docker 注冊表中提取映像(設置為 0 以禁用). 閱讀有關[自定義分析器的](analyzers.html)更多信息. |
| `SAST_DOCKER_CLIENT_NEGOTIATION_TIMEOUT` | 2m | Docker 客戶端協商的時間限制. 使用 Go 的[`ParseDuration`](https://s0golang0org.icopy.site/pkg/time/)解析超時. 有效時間單位為`ns` , `us` (或`μs` ), `ms` , `s` , `m` , `h` . 例如`300ms` , `1.5h`或`2h45m` . |
| `SAST_PULL_ANALYZER_IMAGE_TIMEOUT` | 5m | Time limit when pulling the image of an analyzer. Timeouts are parsed using Go’s [`ParseDuration`](https://s0golang0org.icopy.site/pkg/time/). Valid time units are `ns`, `us` (or `μs`), `ms`, `s`, `m`, `h`. For example, `300ms`, `1.5h` or `2h45m`. |
| `SAST_RUN_ANALYZER_TIMEOUT` | 20m | 運行分析儀的時間限制. 使用 Go 的[`ParseDuration`](https://s0golang0org.icopy.site/pkg/time/)解析超時. 有效時間單位為`ns` , `us` (或`μs` ), `ms` , `s` , `m` , `h` . 例如`300ms` , `1.5h`或`2h45m` . |
#### Analyzer settings[](#analyzer-settings "Permalink")
某些分析儀可以使用環境變量進行自定義.
| Environment variable | Analyzer | Description |
| --- | --- | --- |
| `SCAN_KUBERNETES_MANIFESTS` | Kubesec | 設置為`"true"`以掃描 Kubernetes 清單. |
| `KUBESEC_HELM_CHARTS_PATH` | Kubesec | `helm`將用于生成`kubesec`將掃描的 Kubernetes 清單的舵圖的可選路徑. 如果定義了`helm dependency build`則應在`before_script`運行`helm dependency build`以獲取必要的依賴關系. |
| `KUBESEC_HELM_OPTIONS` | Kubesec | `helm`可執行文件的其他參數. |
| `COMPILE` | SpotBugs | 設置為`false`可禁用項目編譯和依賴項獲取. 在 GitLab 13.1 中[引入](https://gitlab.com/gitlab-org/gitlab/-/issues/195252) . |
| `ANT_HOME` | SpotBugs | `ANT_HOME`環境變量. |
| `ANT_PATH` | SpotBugs | `ant`可執行文件的路徑. |
| `GRADLE_PATH` | SpotBugs | `gradle`可執行文件的路徑. |
| `JAVA_OPTS` | SpotBugs | `java`可執行文件的附加參數. |
| `JAVA_PATH` | SpotBugs | `java`可執行文件的路徑. |
| `SAST_JAVA_VERSION` | SpotBugs | 使用哪個 Java 版本. 支持的版本是`8`和`11` . 默認為`8` . |
| `MAVEN_CLI_OPTS` | SpotBugs | `mvn`或`mvnw`可執行文件的其他參數. |
| `MAVEN_PATH` | SpotBugs | `mvn`可執行文件的路徑. |
| `MAVEN_REPO_PATH` | SpotBugs | Maven 本地存儲庫的路徑( `maven.repo.local`屬性的快捷方式). |
| `SBT_PATH` | SpotBugs | `sbt`可執行文件的路徑. |
| `FAIL_NEVER` | SpotBugs | 設置為`1`可忽略編譯失敗. |
| `SAST_GOSEC_CONFIG` | Gosec | Gosec 的配置路徑(可選). |
| `PHPCS_SECURITY_AUDIT_PHP_EXTENSIONS` | phpcs-security-audit | 以逗號分隔的其他 PHP 擴展列表. |
| `SEARCH_MAX_DEPTH` | any | 搜索源代碼文件時遍歷的最大目錄數. 默認值: `4` . |
#### Custom environment variables[](#custom-environment-variables "Permalink")
在 GitLab Ultimate 12.5 中[引入](https://gitlab.com/gitlab-org/gitlab/-/merge_requests/18193) .
除上述 SAST 配置變量外,如果[使用 SAST 供應商模板](#configuration) ,則所有[自定義環境變量](../../../ci/variables/README.html#custom-environment-variables)都將傳播到基礎 SAST 分析器映像.
**警告:**名稱以這些前綴開頭的變量將**不會**傳播到 SAST Docker 容器和/或分析器容器: `DOCKER_` , `CI` , `GITLAB_` , `FF_` , `HOME` , `PWD` , `OLDPWD` , `PATH` , `SHLVL` , `HOSTNAME` .
## Reports JSON format[](#reports-json-format "Permalink")
SAST 工具會發出 JSON 報告文件. 有關更多信息,請參見此[報告](https://gitlab.com/gitlab-org/security-products/security-report-schemas/-/blob/master/dist/sast-report-format.json)的[架構](https://gitlab.com/gitlab-org/security-products/security-report-schemas/-/blob/master/dist/sast-report-format.json) .
這是一個示例 SAST 報告:
```
{ "version": "2.0", "vulnerabilities": [ { "id": "9e96e0ab-23da-4d7d-a09e-0acbaa5e83ca", "category": "sast", "name": "Predictable pseudorandom number generator", "message": "Predictable pseudorandom number generator", "description": "The use of java.util.Random is predictable", "severity": "Medium", "confidence": "Medium", "scanner": { "id": "find_sec_bugs", "name": "Find Security Bugs" }, "location": { "file": "groovy/src/main/groovy/com/gitlab/security_products/tests/App.groovy", "start_line": 47, "end_line": 47, "class": "com.gitlab.security_products.tests.App", "method": "generateSecretToken2", "dependency": { "package": {} } }, "identifiers": [ { "type": "find_sec_bugs_type", "name": "Find Security Bugs-PREDICTABLE_RANDOM", "value": "PREDICTABLE_RANDOM", "url": "https://find-sec-bugs.github.io/bugs.htm#PREDICTABLE_RANDOM" }, { "type": "cwe", "name": "CWE-330", "value": "330", "url": "https://cwe.mitre.org/data/definitions/330.html" } ] }, { "id": "e6dbf91f-4c07-46f7-a365-0169489c27d1", "category": "sast", "message": "Probable insecure usage of temp file/directory.", "severity": "Medium", "confidence": "Medium", "scanner": { "id": "bandit", "name": "Bandit" }, "location": { "file": "python/hardcoded/hardcoded-tmp.py", "start_line": 10, "end_line": 10, "dependency": { "package": {} } }, "identifiers": [ { "type": "bandit_test_id", "name": "Bandit Test ID B108", "value": "B108", "url": "https://docs.openstack.org/bandit/latest/plugins/b108_hardcoded_tmp_directory.html" } ] }, ], "remediations": [] }
```
## Secret detection[](#secret-detection "Permalink")
了解有關[秘密檢測的](../secret_detection)更多信息.
## Security Dashboard[](#security-dashboard "Permalink")
在"安全儀表板"中,您可以概覽您的組,項目和管道中的所有安全漏洞. 閱讀有關[安全儀表板的](../security_dashboard/index.html)更多[信息](../security_dashboard/index.html) .
## Interacting with the vulnerabilities[](#interacting-with-the-vulnerabilities "Permalink")
一旦發現漏洞,便可以與其進行交互. 閱讀有關如何[與漏洞](../index.html#interacting-with-the-vulnerabilities)進行[交互的](../index.html#interacting-with-the-vulnerabilities)更多信息.
## Vulnerabilities database[](#vulnerabilities-database "Permalink")
Vulnerabilities contained within the vulnerability database can be searched and viewed at the [GitLab vulnerability advisory database](https://advisories.gitlab.com).
### Vulnerabilities database update[](#vulnerabilities-database-update "Permalink")
有關漏洞數據庫更新的更多信息,請查看[維護表](../index.html#maintenance-and-update-of-the-vulnerabilities-database) .
## Running SAST in an offline environment[](#running-sast-in-an-offline-environment "Permalink")
對于在通過 Internet 限制,限制或間歇性訪問外部資源的環境中進行自我管理的 GitLab 實例,需要進行一些調整才能使 SAST 作業成功運行. 有關更多信息,請參閱[脫機環境](../offline_deployments/index.html) .
### Requirements for offline SAST[](#requirements-for-offline-sast "Permalink")
要在離線環境中使用 SAST,您需要:
* 保持 Docker-In-Docker 禁用(默認).
* GitLab 亞軍與[`docker`或`kubernetes`執行](#requirements) .
* Docker Container Registry,帶有本地可用的 SAST [分析器](https://gitlab.com/gitlab-org/security-products/analyzers)映像副本.
**注意:** GitLab Runner 的[默認`pull policy`為`always`](https://docs.gitlab.com/runner/executors/docker.html) ,這意味著即使本地副本可用,Runner 也會嘗試從 GitLab 容器注冊表中拉取 Docker 映像. 如果您只喜歡使用本地可用的 Docker 映像,則可以在離線環境[`pull_policy`](https://docs.gitlab.com/runner/executors/docker.html) GitLab Runner 的[`pull_policy`設置為`if-not-present`](https://docs.gitlab.com/runner/executors/docker.html) . 但是,如果不在離線環境中,我們建議將拉取策略設置保持為`always` ,因為這樣可以在 CI / CD 管道中使用更新的掃描儀.
### Make GitLab SAST analyzer images available inside your Docker registry[](#make-gitlab-sast-analyzer-images-available-inside-your-docker-registry "Permalink")
對于具有所有[受支持的語言和框架的](#supported-languages-and-frameworks) SAST,請將以下默認 SAST 分析器圖像從`registry.gitlab.com`導入[本地 Docker 容器注冊表](../../packages/container_registry/index.html) :
```
registry.gitlab.com/gitlab-org/security-products/analyzers/bandit:2
registry.gitlab.com/gitlab-org/security-products/analyzers/brakeman:2
registry.gitlab.com/gitlab-org/security-products/analyzers/eslint:2
registry.gitlab.com/gitlab-org/security-products/analyzers/flawfinder:2
registry.gitlab.com/gitlab-org/security-products/analyzers/gosec:2
registry.gitlab.com/gitlab-org/security-products/analyzers/kubesec:2
registry.gitlab.com/gitlab-org/security-products/analyzers/nodejs-scan:2
registry.gitlab.com/gitlab-org/security-products/analyzers/phpcs-security-audit:2
registry.gitlab.com/gitlab-org/security-products/analyzers/pmd-apex:2
registry.gitlab.com/gitlab-org/security-products/analyzers/secrets:2
registry.gitlab.com/gitlab-org/security-products/analyzers/security-code-scan:2
registry.gitlab.com/gitlab-org/security-products/analyzers/sobelow:2
registry.gitlab.com/gitlab-org/security-products/analyzers/spotbugs:2
```
將 Docker 映像導入本地脫機 Docker 注冊表的過程取決于**您的網絡安全策略** . 請咨詢您的 IT 員工,以找到可以導入或臨時訪問外部資源的已接受和批準的流程. 請注意,這些掃描程序會[定期](../index.html#maintenance-and-update-of-the-vulnerabilities-database)使用新定義進行[更新](../index.html#maintenance-and-update-of-the-vulnerabilities-database) ,因此請考慮您是否能夠自己進行定期更新.
有關將 Docker 映像保存和傳輸為文件的詳細信息,請參閱 Docker 有關[`docker save`](https://s0docs0docker0com.icopy.site/engine/reference/commandline/save/) , [`docker load`](https://s0docs0docker0com.icopy.site/engine/reference/commandline/load/) , [`docker export`](https://s0docs0docker0com.icopy.site/engine/reference/commandline/export/)和[`docker import`](https://s0docs0docker0com.icopy.site/engine/reference/commandline/import/)的文檔.
### Set SAST CI job variables to use local SAST analyzers[](#set-sast-ci-job-variables-to-use-local-sast-analyzers "Permalink")
將以下配置添加到您的`.gitlab-ci.yml`文件. 您必須替換`SECURE_ANALYZERS_PREFIX`才能引用本地 Docker 容器注冊表:
```
include:
- template: SAST.gitlab-ci.yml
variables:
SECURE_ANALYZERS_PREFIX: "localhost:5000/analyzers"
```
現在,SAST 作業應使用 SAST 分析器的本地副本來掃描您的代碼并生成安全報告,而無需訪問 Internet.
## Troubleshooting[](#troubleshooting "Permalink")
### `Error response from daemon: error processing tar file: docker-tar: relocation error`[](#error-response-from-daemon-error-processing-tar-file-docker-tar-relocation-error "Permalink")
當運行 SAST 作業的碼頭工人的版本是出現此錯誤`19.03.0` . 考慮更新到 Docker `19.03.1`或更高版本. 舊版本不受影響. 閱讀[本期的](https://gitlab.com/gitlab-org/gitlab/-/issues/13830#note_211354992 "當前的 SAST 容器失敗")更多內容.
- GitLab Docs
- Installation
- Requirements
- GitLab cloud native Helm Chart
- Install GitLab with Docker
- Installation from source
- Install GitLab on Microsoft Azure
- Installing GitLab on Google Cloud Platform
- Installing GitLab on Amazon Web Services (AWS)
- Analytics
- Code Review Analytics
- Productivity Analytics
- Value Stream Analytics
- Kubernetes clusters
- Adding and removing Kubernetes clusters
- Adding EKS clusters
- Adding GKE clusters
- Group-level Kubernetes clusters
- Instance-level Kubernetes clusters
- Canary Deployments
- Cluster Environments
- Deploy Boards
- GitLab Managed Apps
- Crossplane configuration
- Cluster management project (alpha)
- Kubernetes Logs
- Runbooks
- Serverless
- Deploying AWS Lambda function using GitLab CI/CD
- Securing your deployed applications
- Groups
- Contribution Analytics
- Custom group-level project templates
- Epics
- Manage epics
- Group Import/Export
- Insights
- Issues Analytics
- Iterations
- Public access
- SAML SSO for GitLab.com groups
- SCIM provisioning using SAML SSO for GitLab.com groups
- Subgroups
- Roadmap
- Projects
- GitLab Secure
- Security Configuration
- Container Scanning
- Dependency Scanning
- Dependency List
- Static Application Security Testing (SAST)
- Secret Detection
- Dynamic Application Security Testing (DAST)
- GitLab Security Dashboard
- Offline environments
- Standalone Vulnerability pages
- Security scanner integration
- Badges
- Bulk editing issues and merge requests at the project level
- Code Owners
- Compliance
- License Compliance
- Compliance Dashboard
- Create a project
- Description templates
- Deploy Keys
- Deploy Tokens
- File finder
- Project integrations
- Integrations
- Atlassian Bamboo CI Service
- Bugzilla Service
- Custom Issue Tracker service
- Discord Notifications service
- Enabling emails on push
- GitHub project integration
- Hangouts Chat service
- Atlassian HipChat
- Irker IRC Gateway
- GitLab Jira integration
- Mattermost Notifications Service
- Mattermost slash commands
- Microsoft Teams service
- Mock CI Service
- Prometheus integration
- Redmine Service
- Slack Notifications Service
- Slack slash commands
- GitLab Slack application
- Webhooks
- YouTrack Service
- Insights
- Issues
- Crosslinking Issues
- Design Management
- Confidential issues
- Due dates
- Issue Boards
- Issue Data and Actions
- Labels
- Managing issues
- Milestones
- Multiple Assignees for Issues
- Related issues
- Service Desk
- Sorting and ordering issue lists
- Issue weight
- Associate a Zoom meeting with an issue
- Merge requests
- Allow collaboration on merge requests across forks
- Merge Request Approvals
- Browser Performance Testing
- How to create a merge request
- Cherry-pick changes
- Code Quality
- Load Performance Testing
- Merge Request dependencies
- Fast-forward merge requests
- Merge when pipeline succeeds
- Merge request conflict resolution
- Reverting changes
- Reviewing and managing merge requests
- Squash and merge
- Merge requests versions
- Draft merge requests
- Members of a project
- Migrating projects to a GitLab instance
- Import your project from Bitbucket Cloud to GitLab
- Import your project from Bitbucket Server to GitLab
- Migrating from ClearCase
- Migrating from CVS
- Import your project from FogBugz to GitLab
- Gemnasium
- Import your project from GitHub to GitLab
- Project importing from GitLab.com to your private GitLab instance
- Import your project from Gitea to GitLab
- Import your Jira project issues to GitLab
- Migrating from Perforce Helix
- Import Phabricator tasks into a GitLab project
- Import multiple repositories by uploading a manifest file
- Import project from repo by URL
- Migrating from SVN to GitLab
- Migrating from TFVC to Git
- Push Options
- Releases
- Repository
- Branches
- Git Attributes
- File Locking
- Git file blame
- Git file history
- Repository mirroring
- Protected branches
- Protected tags
- Push Rules
- Reduce repository size
- Signing commits with GPG
- Syntax Highlighting
- GitLab Web Editor
- Web IDE
- Requirements Management
- Project settings
- Project import/export
- Project access tokens (Alpha)
- Share Projects with other Groups
- Snippets
- Static Site Editor
- Wiki
- Project operations
- Monitor metrics for your CI/CD environment
- Set up alerts for Prometheus metrics
- Embedding metric charts within GitLab-flavored Markdown
- Embedding Grafana charts
- Using the Metrics Dashboard
- Dashboard YAML properties
- Metrics dashboard settings
- Panel types for dashboards
- Using Variables
- Templating variables for metrics dashboards
- Prometheus Metrics library
- Monitoring AWS Resources
- Monitoring HAProxy
- Monitoring Kubernetes
- Monitoring NGINX
- Monitoring NGINX Ingress Controller
- Monitoring NGINX Ingress Controller with VTS metrics
- Alert Management
- Error Tracking
- Tracing
- Incident Management
- GitLab Status Page
- Feature Flags
- GitLab CI/CD
- GitLab CI/CD pipeline configuration reference
- GitLab CI/CD include examples
- Introduction to CI/CD with GitLab
- Getting started with GitLab CI/CD
- How to enable or disable GitLab CI/CD
- Using SSH keys with GitLab CI/CD
- Migrating from CircleCI
- Migrating from Jenkins
- Auto DevOps
- Getting started with Auto DevOps
- Requirements for Auto DevOps
- Customizing Auto DevOps
- Stages of Auto DevOps
- Upgrading PostgreSQL for Auto DevOps
- Cache dependencies in GitLab CI/CD
- GitLab ChatOps
- Cloud deployment
- Docker integration
- Building Docker images with GitLab CI/CD
- Using Docker images
- Building images with kaniko and GitLab CI/CD
- GitLab CI/CD environment variables
- Predefined environment variables reference
- Where variables can be used
- Deprecated GitLab CI/CD variables
- Environments and deployments
- Protected Environments
- GitLab CI/CD Examples
- Test a Clojure application with GitLab CI/CD
- Using Dpl as deployment tool
- Testing a Phoenix application with GitLab CI/CD
- End-to-end testing with GitLab CI/CD and WebdriverIO
- DevOps and Game Dev with GitLab CI/CD
- Deploy a Spring Boot application to Cloud Foundry with GitLab CI/CD
- How to deploy Maven projects to Artifactory with GitLab CI/CD
- Testing PHP projects
- Running Composer and NPM scripts with deployment via SCP in GitLab CI/CD
- Test and deploy Laravel applications with GitLab CI/CD and Envoy
- Test and deploy a Python application with GitLab CI/CD
- Test and deploy a Ruby application with GitLab CI/CD
- Test and deploy a Scala application to Heroku
- GitLab CI/CD for external repositories
- Using GitLab CI/CD with a Bitbucket Cloud repository
- Using GitLab CI/CD with a GitHub repository
- GitLab Pages
- GitLab Pages
- GitLab Pages domain names, URLs, and baseurls
- Create a GitLab Pages website from scratch
- Custom domains and SSL/TLS Certificates
- GitLab Pages integration with Let's Encrypt
- GitLab Pages Access Control
- Exploring GitLab Pages
- Incremental Rollouts with GitLab CI/CD
- Interactive Web Terminals
- Optimizing GitLab for large repositories
- Metrics Reports
- CI/CD pipelines
- Pipeline Architecture
- Directed Acyclic Graph
- Multi-project pipelines
- Parent-child pipelines
- Pipelines for Merge Requests
- Pipelines for Merged Results
- Merge Trains
- Job artifacts
- Pipeline schedules
- Pipeline settings
- Triggering pipelines through the API
- Review Apps
- Configuring GitLab Runners
- GitLab CI services examples
- Using MySQL
- Using PostgreSQL
- Using Redis
- Troubleshooting CI/CD
- GitLab Package Registry
- GitLab Container Registry
- Dependency Proxy
- GitLab Composer Repository
- GitLab Conan Repository
- GitLab Maven Repository
- GitLab NPM Registry
- GitLab NuGet Repository
- GitLab PyPi Repository
- API Docs
- API resources
- .gitignore API
- GitLab CI YMLs API
- Group and project access requests API
- Appearance API
- Applications API
- Audit Events API
- Avatar API
- Award Emoji API
- Project badges API
- Group badges API
- Branches API
- Broadcast Messages API
- Project clusters API
- Group clusters API
- Instance clusters API
- Commits API
- Container Registry API
- Custom Attributes API
- Dashboard annotations API
- Dependencies API
- Deploy Keys API
- Deployments API
- Discussions API
- Dockerfiles API
- Environments API
- Epics API
- Events
- Feature Flags API
- Feature flag user lists API
- Freeze Periods API
- Geo Nodes API
- Group Activity Analytics API
- Groups API
- Import API
- Issue Boards API
- Group Issue Boards API
- Issues API
- Epic Issues API
- Issues Statistics API
- Jobs API
- Keys API
- Labels API
- Group Labels API
- License
- Licenses API
- Issue links API
- Epic Links API
- Managed Licenses API
- Markdown API
- Group and project members API
- Merge request approvals API
- Merge requests API
- Project milestones API
- Group milestones API
- Namespaces API
- Notes API
- Notification settings API
- Packages API
- Pages domains API
- Pipeline schedules API
- Pipeline triggers API
- Pipelines API
- Project Aliases API
- Project import/export API
- Project repository storage moves API
- Project statistics API
- Project templates API
- Projects API
- Protected branches API
- Protected tags API
- Releases API
- Release links API
- Repositories API
- Repository files API
- Repository submodules API
- Resource label events API
- Resource milestone events API
- Resource weight events API
- Runners API
- SCIM API
- Search API
- Services API
- Application settings API
- Sidekiq Metrics API
- Snippets API
- Project snippets
- Application statistics API
- Suggest Changes API
- System hooks API
- Tags API
- Todos API
- Users API
- Project-level Variables API
- Group-level Variables API
- Version API
- Vulnerabilities API
- Vulnerability Findings API
- Wikis API
- GraphQL API
- Getting started with GitLab GraphQL API
- GraphQL API Resources
- API V3 to API V4
- Validate the .gitlab-ci.yml (API)
- User Docs
- Abuse reports
- User account
- Active sessions
- Deleting a User account
- Permissions
- Personal access tokens
- Profile preferences
- Threads
- GitLab and SSH keys
- GitLab integrations
- Git
- GitLab.com settings
- Infrastructure as code with Terraform and GitLab
- GitLab keyboard shortcuts
- GitLab Markdown
- AsciiDoc
- GitLab Notification Emails
- GitLab Quick Actions
- Autocomplete characters
- Reserved project and group names
- Search through GitLab
- Advanced Global Search
- Advanced Syntax Search
- Time Tracking
- GitLab To-Do List
- Administrator Docs
- Reference architectures
- Reference architecture: up to 1,000 users
- Reference architecture: up to 2,000 users
- Reference architecture: up to 3,000 users
- Reference architecture: up to 5,000 users
- Reference architecture: up to 10,000 users
- Reference architecture: up to 25,000 users
- Reference architecture: up to 50,000 users
- Troubleshooting a reference architecture set up
- Working with the bundled Consul service
- Configuring PostgreSQL for scaling
- Configuring GitLab application (Rails)
- Load Balancer for multi-node GitLab
- Configuring a Monitoring node for Scaling and High Availability
- NFS
- Working with the bundled PgBouncer service
- Configuring Redis for scaling
- Configuring Sidekiq
- Admin Area settings
- Continuous Integration and Deployment Admin settings
- Custom instance-level project templates
- Diff limits administration
- Enable and disable GitLab features deployed behind feature flags
- Geo nodes Admin Area
- GitLab Pages administration
- Health Check
- Job logs
- Labels administration
- Log system
- PlantUML & GitLab
- Repository checks
- Repository storage paths
- Repository storage types
- Account and limit settings
- Service templates
- System hooks
- Changing your time zone
- Uploads administration
- Abuse reports
- Activating and deactivating users
- Audit Events
- Blocking and unblocking users
- Broadcast Messages
- Elasticsearch integration
- Gitaly
- Gitaly Cluster
- Gitaly reference
- Monitoring GitLab
- Monitoring GitLab with Prometheus
- Performance Bar
- Usage statistics
- Object Storage
- Performing Operations in GitLab
- Cleaning up stale Redis sessions
- Fast lookup of authorized SSH keys in the database
- Filesystem Performance Benchmarking
- Moving repositories managed by GitLab
- Run multiple Sidekiq processes
- Sidekiq MemoryKiller
- Switching to Puma
- Understanding Unicorn and unicorn-worker-killer
- User lookup via OpenSSH's AuthorizedPrincipalsCommand
- GitLab Package Registry administration
- GitLab Container Registry administration
- Replication (Geo)
- Geo database replication
- Geo with external PostgreSQL instances
- Geo configuration
- Using a Geo Server
- Updating the Geo nodes
- Geo with Object storage
- Docker Registry for a secondary node
- Geo for multiple nodes
- Geo security review (Q&A)
- Location-aware Git remote URL with AWS Route53
- Tuning Geo
- Removing secondary Geo nodes
- Geo data types support
- Geo Frequently Asked Questions
- Geo Troubleshooting
- Geo validation tests
- Disaster Recovery (Geo)
- Disaster recovery for planned failover
- Bring a demoted primary node back online
- Automatic background verification
- Rake tasks
- Back up and restore GitLab
- Clean up
- Namespaces
- Maintenance Rake tasks
- Geo Rake Tasks
- GitHub import
- Import bare repositories
- Integrity check Rake task
- LDAP Rake tasks
- Listing repository directories
- Praefect Rake tasks
- Project import/export administration
- Repository storage Rake tasks
- Generate sample Prometheus data
- Uploads migrate Rake tasks
- Uploads sanitize Rake tasks
- User management
- Webhooks administration
- X.509 signatures
- Server hooks
- Static objects external storage
- Updating GitLab
- GitLab release and maintenance policy
- Security
- Password Storage
- Custom password length limits
- Restrict allowed SSH key technologies and minimum length
- Rate limits
- Webhooks and insecure internal web services
- Information exclusivity
- How to reset your root password
- How to unlock a locked user from the command line
- User File Uploads
- How we manage the TLS protocol CRIME vulnerability
- User email confirmation at sign-up
- Security of running jobs
- Proxying assets
- CI/CD Environment Variables
- Contributor and Development Docs
- Contribute to GitLab
- Community members & roles
- Implement design & UI elements
- Issues workflow
- Merge requests workflow
- Code Review Guidelines
- Style guides
- GitLab Architecture Overview
- CI/CD development documentation
- Database guides
- Database Review Guidelines
- Database Review Guidelines
- Migration Style Guide
- What requires downtime?
- Understanding EXPLAIN plans
- Rake tasks for developers
- Mass inserting Rails models
- GitLab Documentation guidelines
- Documentation Style Guide
- Documentation structure and template
- Documentation process
- Documentation site architecture
- Global navigation
- GitLab Docs monthly release process
- Telemetry Guide
- Usage Ping Guide
- Snowplow Guide
- Experiment Guide
- Feature flags in development of GitLab
- Feature flags process
- Developing with feature flags
- Feature flag controls
- Document features deployed behind feature flags
- Frontend Development Guidelines
- Accessibility & Readability
- Ajax
- Architecture
- Axios
- Design Patterns
- Frontend Development Process
- DropLab
- Emojis
- Filter
- Frontend FAQ
- GraphQL
- Icons and SVG Illustrations
- InputSetter
- Performance
- Principles
- Security
- Tooling
- Vuex
- Vue
- Geo (development)
- Geo self-service framework (alpha)
- Gitaly developers guide
- GitLab development style guides
- API style guide
- Go standards and style guidelines
- GraphQL API style guide
- Guidelines for shell commands in the GitLab codebase
- HTML style guide
- JavaScript style guide
- Migration Style Guide
- Newlines style guide
- Python Development Guidelines
- SCSS style guide
- Shell scripting standards and style guidelines
- Sidekiq debugging
- Sidekiq Style Guide
- SQL Query Guidelines
- Vue.js style guide
- Instrumenting Ruby code
- Testing standards and style guidelines
- Flaky tests
- Frontend testing standards and style guidelines
- GitLab tests in the Continuous Integration (CI) context
- Review Apps
- Smoke Tests
- Testing best practices
- Testing levels
- Testing Rails migrations at GitLab
- Testing Rake tasks
- End-to-end Testing
- Beginner's guide to writing end-to-end tests
- End-to-end testing Best Practices
- Dynamic Element Validation
- Flows in GitLab QA
- Page objects in GitLab QA
- Resource class in GitLab QA
- Style guide for writing end-to-end tests
- Testing with feature flags
- Translate GitLab to your language
- Internationalization for GitLab
- Translating GitLab
- Proofread Translations
- Merging translations from CrowdIn
- Value Stream Analytics development guide
- GitLab subscription
- Activate GitLab EE with a license
